VMWare
Because VSys Live uses a direct and live connection to your database, it must be hosted someplace with a fast connection to that database. This means that it's generally hosted in your IT department, rather than by an outside organization. We provide VSys Live to you as a pre-configured VMWare environment, suitable for use in any modern VMWare system such as ESX. Within that environment is a copy of Windows Server 2008 R2 Web Edition, loaded with:
Plan to give that VMWare environment:
Note: VSys Live does not store any persistent data within its own environment. Everything important is stored on and retrieved from the VSys One database. This means that backups of the VSys Live session are not critical, and that VSys Live will not grow much in terms of disk space requirements over time.
Network access
For volunteers to access VSys Live, you must pass ports 80 and 443 through your firewall to the VMWare session running VSys Live. (It accepts connections on port 80 only to immediately redirect them to port 443 and a secured session.)
Mail server
To send out password reset notifications and a few other communications, VSys Live needs access to an SMTP relay. Generally this will be a server running on your own network, but it can be an external server. VSys Live can be configured to use SSL connections for SMTP. It does not require any inbound mail (POP3) access.
SSL certificate
All communications with outside entities to VSys Live (volunteers using a web browser) are done using SSL, which provides end-to-end encryption of all data. All SSL certificates are paired with their FQDN, e.g. volunteers.youorg.org. For VSys Live to respond using the URL https://volunteers.yourorg.org, an appropriate SSL certificate for this FQDN, or a wildcard certificate valid for *.yourorg.org, must be acquired by you and installed into VSys Live.
Database access
For VSys Live to work, it obviously must be able to connect to your live VSys One database, generally SQL Server. You'll need to install the VMWare session which runs VSys Live someplace that it can make those connections.
Security
VSys Live uses only secure connections when communicating with outside entities (volunteers). Internally, though, VSys Live connects to VOXI over unsecured, unauthenticated connections for performance reasons. As long as VSys Live and VOXI are running within the same VMWare session, this makes securing VOXI simple: do not allow any inbound connections to that session on the port that VOXI communicates on (generally port 99). If VSys Live and VOXI are separated, you'll want to make sure that the session running VOXI only accepts inbound connections from the session running VSys Live.
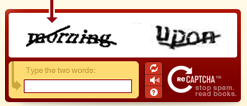
reCAPTCHA
reCAPTCHA is a tool used by many websites to verify that there is a human at the keyboard and not a 'bot. VSys Live requires that you have your own reCAPTCHA account set up. This is a free process.

Sign up for your own reCAPTCHA account on Google's website, and enter the public and private keys into the VSys Live Server Settings.